This article will guide how to stop email spoofing, a prevalent and dangerous cybersecurity problem. We’ll go through several strategies, including staff training, the usage of anti-spoofing technology, and email authentication protocols like DMARC, SPF, and DKIM. You will know more about how to stop email spoofing and defend your company from assaults after the article.
Organizations may use email authentication standards like DMARC, SPF, and DKIM to prevent email spoofing. Moreover, they may deploy anti-spoofing technology, train staff members on email spoofing and phishing, and regularly evaluate and update their email security rules.
You may fully grasp how to stop email spoofing and defend your company from assaults by reading the entire article. Hence we will go through the specifics of email authentication protocols, including DMARC, SPF, and DKIM, and offer helpful implementation advice. We’ll also talk about staff training and using anti-spoofing tools so you can tackle email security holistically.
See Also: 6 Best Email Client For Chromebook Tools Of 2024
Table of Contents
Email Spoofing: What Is It?
Cybercriminals frequently employ email spoofing to deceive users into thinking that an email is from a reliable source. So to make the email look like it has been sent by someone else, forge the sender’s email address.
 Email spoofing is a huge security risk that can harm reputation, finances, and other areas. The purpose of email spoofing can range from collecting sensitive data like login passwords or financial information to deceiving users into clicking on harmful links or installing malware. So we’ll talk about how to stop email spoofing in this article.
Email spoofing is a huge security risk that can harm reputation, finances, and other areas. The purpose of email spoofing can range from collecting sensitive data like login passwords or financial information to deceiving users into clicking on harmful links or installing malware. So we’ll talk about how to stop email spoofing in this article.
See Also: How to Repair the Outlook Signature
Understanding Email Spoofing
Cybercriminals use email spoofing to take advantage of holes in the email infrastructure. However, the email header records the sender and recipient email addresses, transmission metadata, subject line, and body.
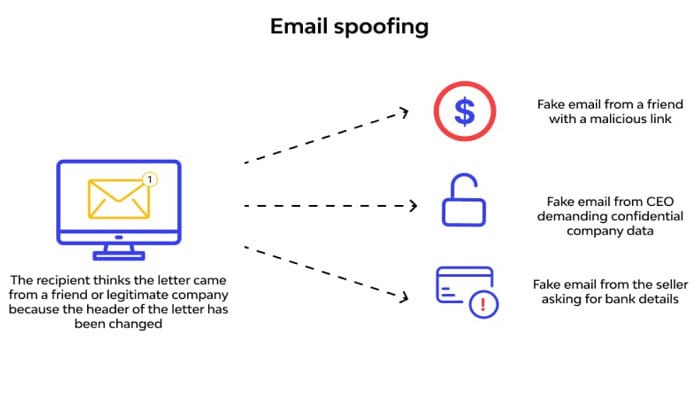 Email spoofing is a technique cybercriminals use to change the sender’s email address in the email header to make an email appear from a reliable person or business. However, phishing attempts frequently employ this technique to coerce victims into providing personal information or clicking on dangerous links. Email spoofing considerably improves the probability that the fraud will be successful by seeming to be a reliable source.
Email spoofing is a technique cybercriminals use to change the sender’s email address in the email header to make an email appear from a reliable person or business. However, phishing attempts frequently employ this technique to coerce victims into providing personal information or clicking on dangerous links. Email spoofing considerably improves the probability that the fraud will be successful by seeming to be a reliable source.
Stopping Email Spoofing
How to stop email spoofing? Fortunately, there are several actions that people and organizations may take to protect against email spoofing. Some actions are as follows:
Implementing DMARC
The acronym for this phrase is Domain-based Message Authentication, Reporting, and Conformance. An email authentication mechanism protects domain owners against unwanted use, including email spoofing. DMARC operates by comparing an array of policies established by the domain owner to the sender’s email address to determine its legitimacy.
DMARC is a useful technique for email spoofing prevention since it allows email providers to stop email spoofing and confirm the legitimacy of emails and reject those that don’t adhere to the set criteria. The use of their domains, including how many emails are sent, who is sending them, and whether they deliver it properly, can be important information for domain owners, thanks to DMARC.
 Hence email domain owners must configure their DNS (Domain Name System) to include a DMARC record to deploy DMARC. The DMARC record specifies the policies you should apply to emails from the domain. Owners of email domains may specify policies ranging from email monitoring to rejecting messages that fail DMARC inspections.
Hence email domain owners must configure their DNS (Domain Name System) to include a DMARC record to deploy DMARC. The DMARC record specifies the policies you should apply to emails from the domain. Owners of email domains may specify policies ranging from email monitoring to rejecting messages that fail DMARC inspections.
See Also: How To Recover A Twitter Account Without Email And Phone Number
Enabling SPF
SPF, or Sender Policy Framework, is the acronym. Domain owners of email addresses designate which email servers can deliver emails. The receiving email server may verify that an email was sent from an authorized server. By prohibiting attackers from sending emails that appear to be from a trustworthy domain, enabling SPF can stop email spoofing. Remembering that attackers can bypass SPF by using more advanced methods is important.
 Email domain owners must add an SPF record to their DNS settings to activate SPF. Which email servers are permitted to send emails on behalf of the domain are specified in the SPF record for stopping email spoofing.
Email domain owners must add an SPF record to their DNS settings to activate SPF. Which email servers are permitted to send emails on behalf of the domain are specified in the SPF record for stopping email spoofing.
Using DKIM
DKIM is the name for DomainKeys Identified Mail. The sender adds a digital signature to the email header when sending an email using DKIM, allowing the recipient’s email server to verify that the intended sender sent the email and remained unaltered during transmission. It is an additional technique for email authentication that can aid in preventing email spoofing with email appending.
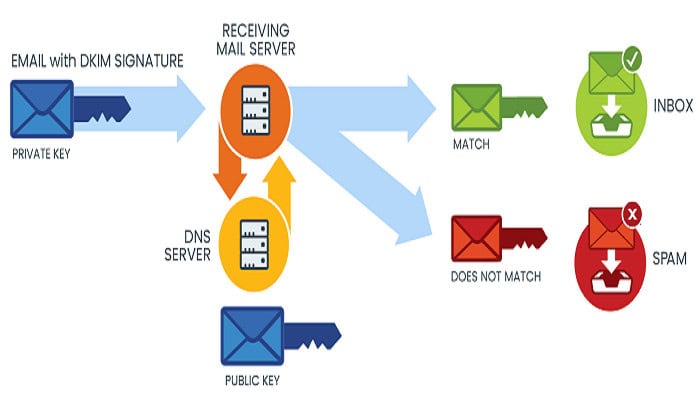 DKIM offers an extra layer of security that you may use in conjunction with SPF and DMARC to stop email spoofing. Collectively, these techniques can aid in limiting the success of attackers in faking email addresses with email sender services.
DKIM offers an extra layer of security that you may use in conjunction with SPF and DMARC to stop email spoofing. Collectively, these techniques can aid in limiting the success of attackers in faking email addresses with email sender services.
Owners of email domains must create a public and private key pair and include the public key in their DNS setup to utilize DKIM. The private key creates the digital signature included in the email header. When the receiving email server receives an email, it can confirm the digital signature and authenticate that the email was sent by a legitimate sender using the public key.
Educating Employees
Employee education on email spoofing and how to spot phishing emails is as important as putting email authentication systems in place. Employers should teach employees to recognize the indicators of a phishing email. Such as dubious links or demands for sensitive information. So you should urge them to stop email spoofing and contact the sender directly or check the sender’s email address to confirm the legitimacy of emails that are from a reliable source for blocking spoofed email.
 Hence regularly training and educating employees can avoid email spoofing and other cybersecurity problems. Workers who are aware of the dangers and are good at spotting and reporting suspicious emails can aid in defending the company against cyberattacks.
Hence regularly training and educating employees can avoid email spoofing and other cybersecurity problems. Workers who are aware of the dangers and are good at spotting and reporting suspicious emails can aid in defending the company against cyberattacks.
Using Anti-Spoofing Technologies
To prevent email spoofing, companies can utilize anti-spoofing solutions. These tools include email authentication tools that can help enforce email authentication protocols like SPF, DKIM, and DMARC, as well as email gateway filters. It can check incoming and outgoing email traffic for indications of spoofing with secure email services.
 However, certain anti-spoofing technology can also deliver in-the-moment warnings. And reports that can aid companies in spotting and promptly countering email spoofing assaults.
However, certain anti-spoofing technology can also deliver in-the-moment warnings. And reports that can aid companies in spotting and promptly countering email spoofing assaults.
FAQs
What does email spoofing entail?
Email spoofing is sending emails with a fake sender address to give the impression that they came from a reliable source. You can use spoof emails to transmit malware, phishing scams, and other crimes.
Why does email spoofing pose a security risk?
Because you may use it to fool receivers into giving up important information or installing malware, email spoofing poses a security risk. In addition to costing the receiver money, forged emails can harm the sender's reputation.
What exactly is DMARC?
To confirm the legitimacy of email communications, the DMARC email authentication standard is employed. By enabling email domain owners to post policies that outline how email communications from their domain should be treated by receiving email servers. It intends to deter email spoofing and phishing assaults.
SPF: What is it?
To confirm that you delivered an email message from a trusted sender, SPF is a mechanism for email authentication. It lets owners of email domains choose which IP addresses allows sending emails on behalf of their domains.
DKIM, what is it?
Add a digital signature to emails using the email authentication protocol DKIM. Receiving email servers may confirm that an email was sent by an authorized sender and was not tampered with during transmission using the digital signature.
How can businesses stop email spoofing?
By deploying email authentication standards like DMARC, SPF, and DKIM, organizations may stop email spoofing. Moreover, they may deploy anti-spoofing technology, train staff members on email spoofing and phishing, and regularly evaluate and update their email security rules.
Conclusion
In this article, we covered how to stop email spoofing and discussed various strategies that one can implement to stop spoofing email. You can shield organizations and clients from the devastating repercussions of cybercrime by taking proactive steps to avoid email spoofing. Spoofing emails pose a serious security risk and can harm one’s reputation and cost money.
By adopting email authentication methods, training staff, and utilizing anti-spoofing technology, and organizations may prevent assaults. Taking a complete approach that incorporates technological fixes and personnel training is vital. To remain successful against the most recent cyber dangers, it is also essential to regularly examine email security protocols.




